Deanonymization by Sharing YouTube Links
TLDR: Sharing links, especially from centralized clearnet websites can deanonymize the account the link is being shared on
This post will detail the common mistakes of how identities get tied back to otherwise anonymous accounts by sharing links. We will use YouTube as an example, but the principles are broadly applicable to any sharing of links. You could easily replace YouTube with any other public site that you use.
The scenarios discussed will be hypothetical, but the attack vectors are real. See the story of IntelBroker for a real life example.
Why this is important
Any online identities that you would like to remain anonymous will be compromised if you make these mistakes. In addition, Google (who owns YouTube) will be able to correlate all data to your specific identity which law enforcement could subpoena.
It doesn't take long browsing on Dread to find YouTube links being shared. Presumably, the above Dread user would like to stay anonymous. If they made any of the OPSEC mistakes we will detail, this online identity would be completely compromised.
Mistake 1: Account isolation
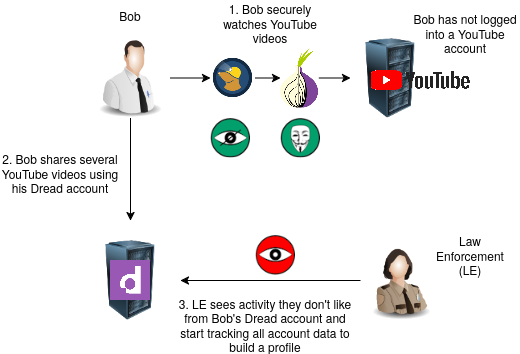
Any sensitive accounts should be assumed to be watched by law enforcement if they are publicly available, even on the darknet. If law enforcement notices that an account on Dread has been making posts sharing information on how to conduct illegal activities or simply sharing a post they don't like, they will then try to link the Dread account to a real life identity.
Let's say that Bob shares a bunch of YouTube videos related to different hobbies of his. Bob essentially handed law enforcement a copy of his watch list via the Dread account, even if he had perfect anonymity on the YouTube end. As explained in the anonymity blog, given enough information about an identity, law enforcement can uniquely identify it.
Any publicly shared link helps law enforcement build a profile of the online identity. As we will further discuss later, every external site linked also increases Bob's attack surface because a slip up on any one of those sites could tie his Dread user identity to an external identity such as his YouTube user.
To protect against information leakage, Bob should have kept his various accounts isolated and avoided using a single account for too long. Avoiding sharing personal information such as hobbies on sensitive accounts means law enforcement first has to at least establish a link between his public and sensitive accounts first. Ideally, Bob doesn't share any personal information even on public accounts.
In addition, Bob should have "rotated" his accounts - meaning to retire his old accounts forever and create an entirely new online identity. This keeps activities and OPSEC mistakes even further siloed.
Mistake 2: Using an Account Linked to Your Identity
This is the most basic but also very common mistake made.
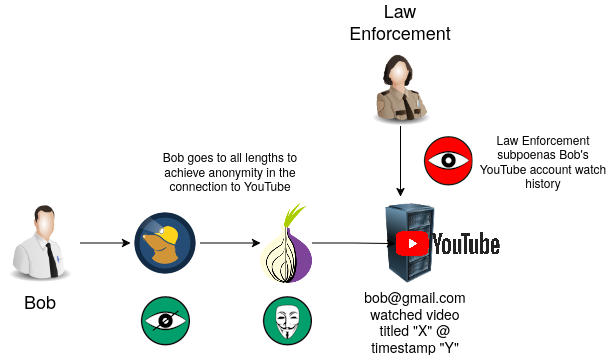
Bob has practiced perfect OPSEC to protect his identity in his connection to YouTube. However, he was logged into his YouTube account which is tied to his email and phone number. Using his private, sensitive account, Bob shared this YouTube video on Dread.
Law enforcement subpoenaed the complete list of viewers who watched this YouTube video. Bob's YouTube account was the only viewer of the video in the recent time span of when he shared it. Given that this YouTube account is tied directly to Bob's real life identity, law enforcement can now easily trace the account back to him.
Bob should have never logged into his YouTube account, especially if he intended to share the video elsewhere. Instead, he should have read the blog post on using Invidious to browse YouTube privately which would also protect him from other ways that his identity can leak outside just the YouTube account.
Never use a public account if the intention is to be browsing in private, especially if planning to share a link elsewhere.
Mistake 3: Browsing with Bad OPSEC
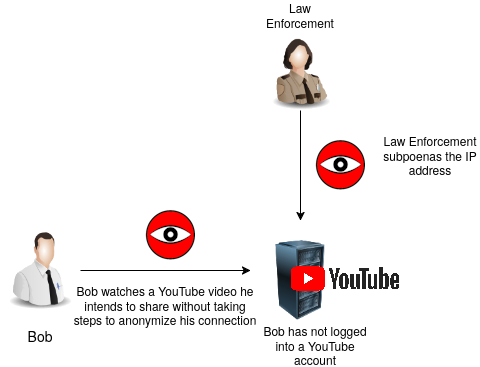
In this scenario, Bob has not logged into his YouTube account. However, the necessary OPSEC precautions have not been taken which exposes his IP address to YouTube.
Law Enforcement can first subpoena the IP addresses of all the viewers of the YouTube video that they found on the sensitive Dread user's account. Turns out that there was only one IP that watched the YouTube video around the same time that the link to the video was shared on Dread. Law enforcement can then subpoena the Internet Service Provider to get the information on Bob's identity and address.
At a minimum, Bob should have read the blog post on browsing privately via Tor. There are too many risks to list everything here. He should evaluate every point at which his data could be compromised, and use the operation security section in this blog if he needs help.
Mistake 4: Sharing Dirty Links
Bob has taken all precautionary measures to avoid the mistakes mentioned above. Bob now clicks the Share button on the YouTube homepage and receives a link with the format:
https://youtu.be/[video-identifier]?si=[source-identifier]
Bob even retires his old online identity and creates a new identity. However, he continues to share videos with the same source identifier.
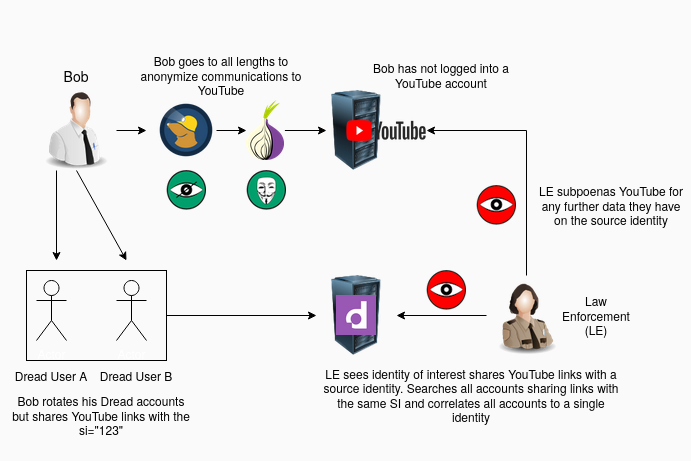
Despite taking all other precautions and not using a YouTube account, Bob has deanonymized himself. Law enforcement can use the source identity to track his watch list and build a profile of him.
Even worse, Law enforcement can search Dread for all account sharing the YouTube link with the same source identity. They now know that all these accounts belong to the same identity.
Bob should have taken the simple step to clean his links before sharing them by stripping the source identifier from the URL:
https://youtu.be/[video-identifier]
Alternatively, Bob could have simply used a private frontend like Invidious from the very beginning.
Either option would have preserved the protection he gained from rotating his old Dread user to stay anonymous.
Conclusion
As previously stated these mistakes are broadly applicable to any centralized, publicly facing site. There are legitimate reasons to need to share a link. However, you should try to be as safe as possible when doing so.
At a minimum do the following checklist:
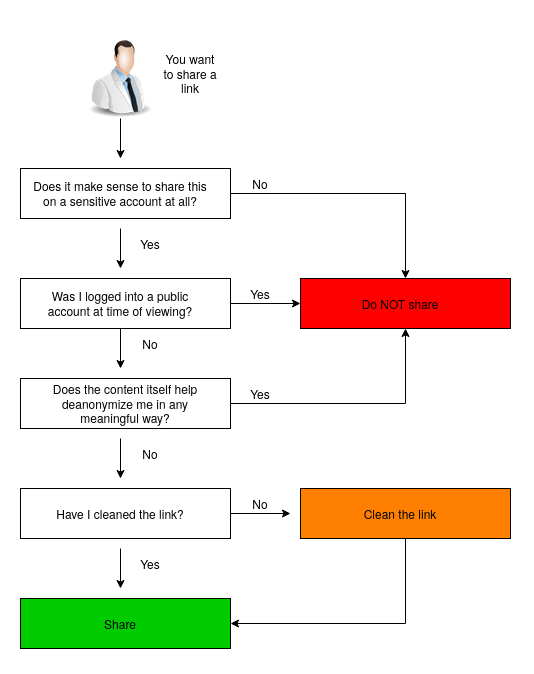
Also consider the following:
- Periodically rotate all your online identities and restart with fresh identities
- Whether you need an account on any particular centralized, public platform at all (you probably don't)
Suggest changes
serpent 2025-11-11
Donate XMR to the author:
88i6jdLdLkPjf1XEFtR7NPDtGkXa42NGwL8pf8LC4TQ7MVJrdvsiAexgEGt1FmTRUGX25Lhnktox7ULDdw221pnmBYMg33m



